For your emails to reach the right people, they need to be delivered. And between pressing send and the recipient opening your email, there are a few things that could go wrong.
Some, like typos in the address, are pretty simple. Others, like authentication, can be quite complicated.
Email authentication identifies your emails as being genuine.
For instance, you need to be authenticated when buying something with your credit card. It’s the same when logging into your favorite social media account or proving to a healthcare provider that you have health insurance. In all these cases, you identify yourself, a system verifies if it is you, and then allows the action to complete.
In contrast to the above example, though, for your emails to be delivered, you won’t use a password or card but rather a set of authentication methods.
In this post, I’ll show you what you need to know about the three key methods (SPF, DKIM, and DMARC).
Let’s dive in!
What Are SPF, DKIM, and DMARC?
SPM, DKIM, and DMARC are all email authentication tools that not only prove that your emails are genuine but also prevent your emails from ending up in recipients’ spam folders.
What Is SPF?
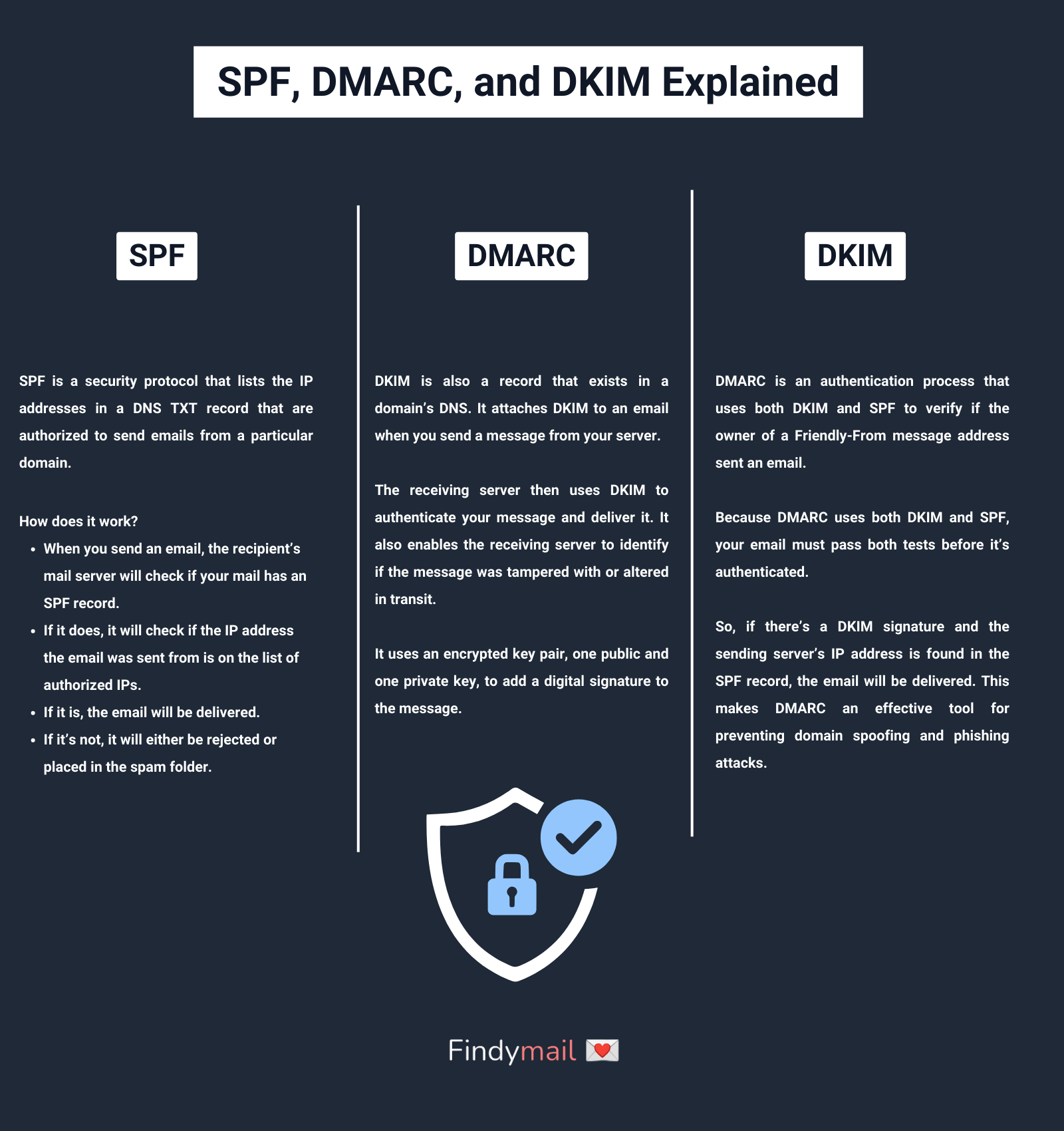
SPF or Sender Policy Framework is a security protocol that lists the IP addresses in a DNS TXT record that are authorized to send emails from a particular domain. So, SPF shows that an email does come from your email server.
But how does SPF work?
- When you send an email, the recipient’s mail server will check if your mail has an SPF record.
- If it does, it will check if the IP address the email was sent from is on the list of authorized IPs.
- If it is, the email will be delivered.
- If it’s not, it will either be rejected or placed in the spam folder.
Let’s assume you’re looking for a Mr. Smith who works for a company in Chicago. You, unfortunately, don’t know which company he works for. So, you decide to call every company. The first thing you’ll ask is if he works there. If he doesn’t, you’ll end the call. If he does, though, you’ll ask to speak to him.
Another way to think of SPF is like you entering your PIN when drawing money. If it’s the wrong PIN, the transaction won’t proceed. In other words, SPF provides authentication information from the outset.
While SPF is reasonably effective at preventing email spoofing or spamming, it does have some limitations. Also, it doesn’t work when emails are forwarded.
What Is DKIM?
DKIM, or DomainKeys Identified Mail, was developed to eliminate SPF’s limitations. Like SPF, DKIM is also a record that exists in a domain’s DNS. It attaches DKIM to an email when you send a message from your server.
The receiving server then uses DKIM to authenticate your message and deliver it. It also enables the receiving server to identify if the message was tampered with or altered in transit.
It uses an encrypted key pair, one public and one private key, to add a digital signature to the message.
Here, one key will be used to decrypt the other key’s encryption. So, the digital signature will then be decrypted when you send an email message. If it matches the information in the unencrypted header of the email, the receiving server will deliver the email.
The simplest way to understand DKIM encryption is to equate it to a lock and key. With the right key, you’ll be able to open the lock. Conversely, with the wrong key, the lock stays shut.
What Is DMARC?
Finally, DMARC, or Domain-Based Message Authentication Reporting and Conformance, is an authentication tool that uses both DKIM and SPF to verify if an email was sent by the owner of a Friendly-From address of a message.
Because DMARC uses both DKIM and SPF, your email must pass both tests before it’s authenticated.
So, if there’s a DKIM signature and the sending server’s IP address is found in the SPF record, the email will be delivered. This makes DMARC an effective tool for preventing domain spoofing and phishing attacks.
A perfect analogy would be where you, besides locks on your doors, also have an alarm system in your home. This means you’ll need both the key and access code for the alarm to enter your home. Without them, you won’t be able to open the door, or the alarm will trigger.
It goes further than this, though. Apart from email authentication, DMARC also allows domain owners to specify what should happen to an email when it’s not authenticated.
Domain owners can set different policies in the DNS record:
- none. In this instance, the receiving server will take no action, and the message will be delivered as usual. Your deliverability won’t be impacted, but you’ll also not be protected against spam.
- quarantine. With this policy, all emails sent from your server that don’t pass the DMARC process will be sent to the recipient’s spam inboxes.
- reject. With this policy, as the name implies, all emails that don’t pass DMARC authentication will bounce. This makes it the most effective method to combat spam, but it could have negative consequences if your DNS records aren’t configured correctly.
Other Email Deliverability Considerations
Now that you know how SPF, DKIM, and DMARC work, you’ll be able to configure them correctly to keep your email deliverability intact. And while you’re at it, make sure you practice good (cold) email hygiene:
- Warm up your inboxes before cold outreach
- Verify your lead list email addresses before you send emails
- Personalize your emails and use spintax to randomize them
With the foundations in place, you’ll be good to go!